Explain Different Application of Ip Security
The application layer of TCPIP model provides applications the ability to access to services of the other layers and defines the protocols that applications use to exchange data. There is a growing need to protect private information crossing the public networks that make up the Internet infrastructure.
Ipsec Architecture Geeksforgeeks
The Internet was not created with security in mind.
. A dynamic packet filter is a firewall facility that can monitor the state of active connections and use this information to determine which network packet s to allow through the firewall. The most popular forms are web application and e-mail. Encryption at the application or the transport layers of the Open Systems Interconnection OSI model can securely transmit data without using IPsec.
Read what 700 CISOs say about DevOps and application security best practices. The reason here is two fold. While using a service from any server application the client and server.
Enhancing electronic commerce security. Finding the right network security tools to secure your sensitive data can be a significant challenge for any organization. The term spoofing might have a comic implication in some contexts but its no joke when it comes to information security.
Authentication procedures ensure that a. Secure remote access over the Internet. Antivirus and Antimalware Software.
Choosing a firewall may seem like a simple task but companies can get overwhelmed by the different firewall types and options. Establishing extranet and intranet connectivity with partners. Most widely-known application layer protocols include HTTP FTP SMTP Telnet DNS SNMP and Routing Information Protocol RIP.
Prevent any type of DDoS attack of any size from preventing access to your. Network Security Application Layer. First if a hacker is able to gain access to a system using someone from marketings credentials you need to prevent the hacker from roaming into other more sensitive.
Communications can be altered examined and exploited. SSL protocol has become the worlds most popular web. It is also one of the applications of digital image processing.
Developers can also code applications to reduce security vulnerabilities. Application security best practices as well as guidance from network security limit access to applications and data to only those who need it. Ad Accelerate application security with 100 automation.
The Imperva applicati on security solution includes. In fact this is a subject matter of a whole separate chapter in a seasoned cybercriminals handbook. At the application layer Hypertext Transfer Protocol Secure performs the encryption.
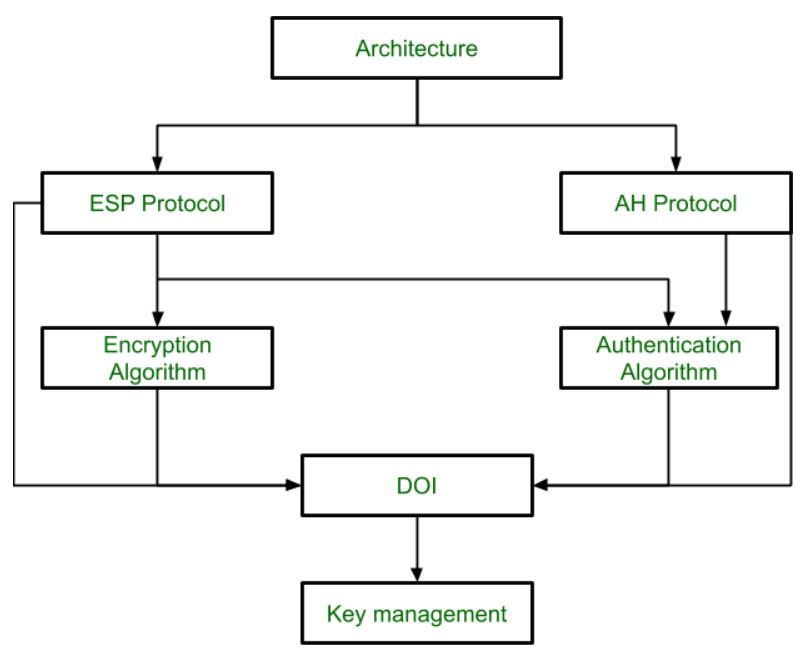
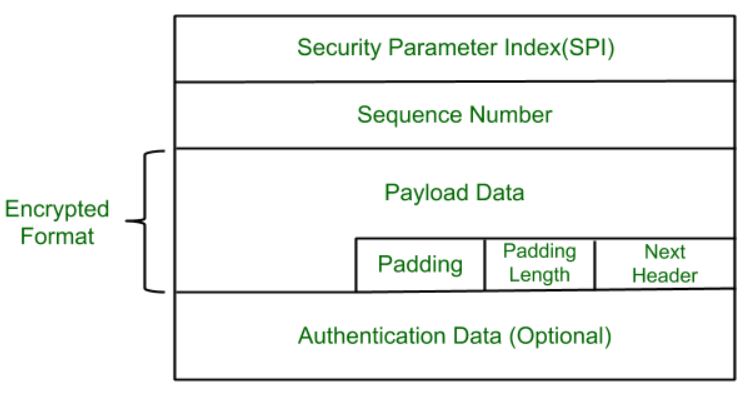
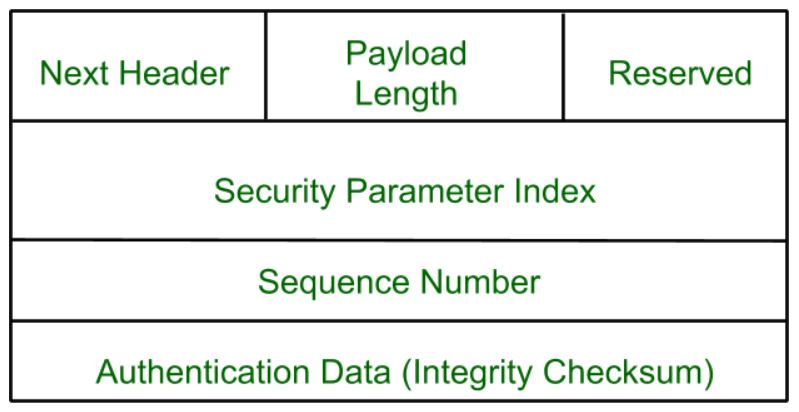
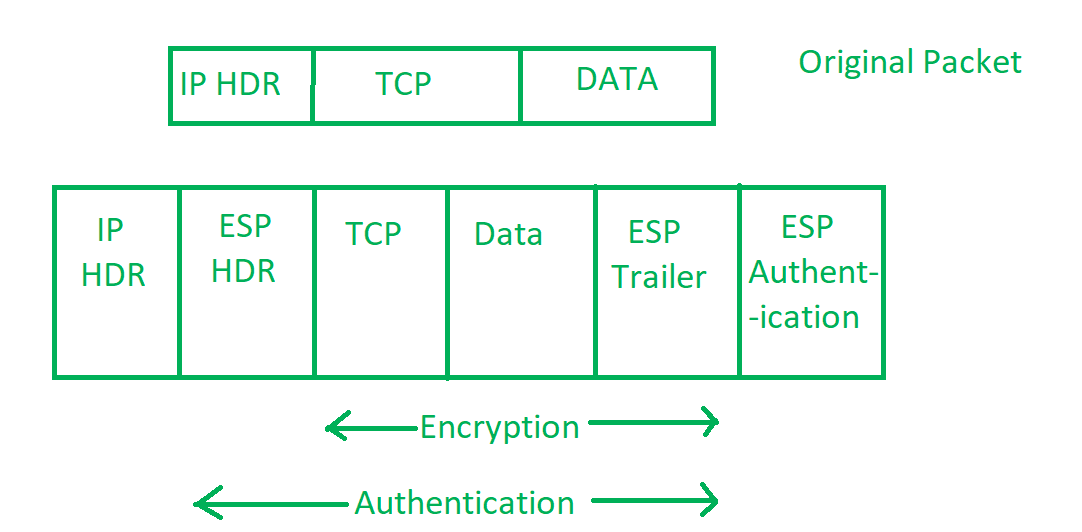
The AH protocol provides service of data integrity and origin authentication. A collection of frames or pictures are arranged in such a way that it makes the fast movement of pictures. When software developers build procedures into an application to ensure that only authorized users gain access to it.
It involves frame rate conversion motion detection reduction of noise and colour space conversion etc. Next Topic Concept of Dimensions. Various business services are now offered online though client-server applications.
Making the distinction between a firewall and other security solutions can. It provides two basic security services like authentication and confidentiality. Different types of application security features include authentication authorization encryption logging and application security testing.
By recording session information such as IP address es and port numbers a dynamic packet filter can implement a much tighter security. Out of all the. There are two security protocols defined by IPsec Authentication Header AH and Encapsulating Security Payload ESP.
It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Answer 1 of 3. While at the transport layer the Transport Layer Security protocol provides the encryption.
However encrypting and authenticating at these. In both applications the client communicates to the designated server and obtains services. DDoS Protectionmaintain uptime in all situations.
Applications of IP Security Secure branch office connectivity over the Internet. Security associations between the communicating entities are established and maintained by the security protocol used. This blog was written by a third party author.
Besides the obvious reasons malware can be very dangerous because sometimes it can will stay calm within your network for days and weeks just sitting there ready to spring up and attack. This software is used to protect against malware which includes anything from viruses Trojans ransomware or spyware. To secure applications and networks across the OSI stack Imperva provides multi-layered protection to make sure websites and applications are available easily accessible and safe.
SSL Protocol stands for Secure Socket Layer protocol which is an internet security protocol used for exchanging the information between a web browser and a web server in a secure manner.

Ipsec Architecture Geeksforgeeks
Static Vs Dynamic Ip Addresses What S The Difference Avast
0 Response to "Explain Different Application of Ip Security"
Post a Comment